The Cyber Vigil Pro Platform
Agentless network security that detects threats, identifies vulnerabilities, and provides AI-powered analysis — without disrupting your operations.
The Problem with Traditional Security
Legacy security solutions create as many problems as they solve. Here’s what you’re up against.
🚫 VPN Vulnerabilities
VPNs create single points of failure. Once breached, attackers have unrestricted lateral movement across your entire network.
🚫 Virtual Machine Overhead
VM-based security consumes significant resources, introduces latency, and requires constant maintenance and patching.
🚫 EDR Agent Conflicts
Endpoint agents conflict with legacy software, OT systems, and non-standard operating systems — leaving critical assets unprotected.
🚫 Alert Fatigue
Security teams drown in thousands of alerts daily, missing real threats buried in the noise of false positives.
The Cyber Vigil Pro Solution
Purpose-built security that works with your network, not against it.
Agentless Detection
- Zero software installation required
- Works with any OS or device
- No performance impact
- Instant deployment
True Isolation
- Network segmentation
- East-west traffic monitoring
- Real-time threat detection
- Zero lateral movement
AI-Powered Analysis
- Executive summaries on demand
- Natural language queries
- Automated threat correlation
- Intelligent prioritization
ICS/OT Protection
- Non-standard OS detection
- Behavioral identification
- Zero network interference
- Industrial protocol support
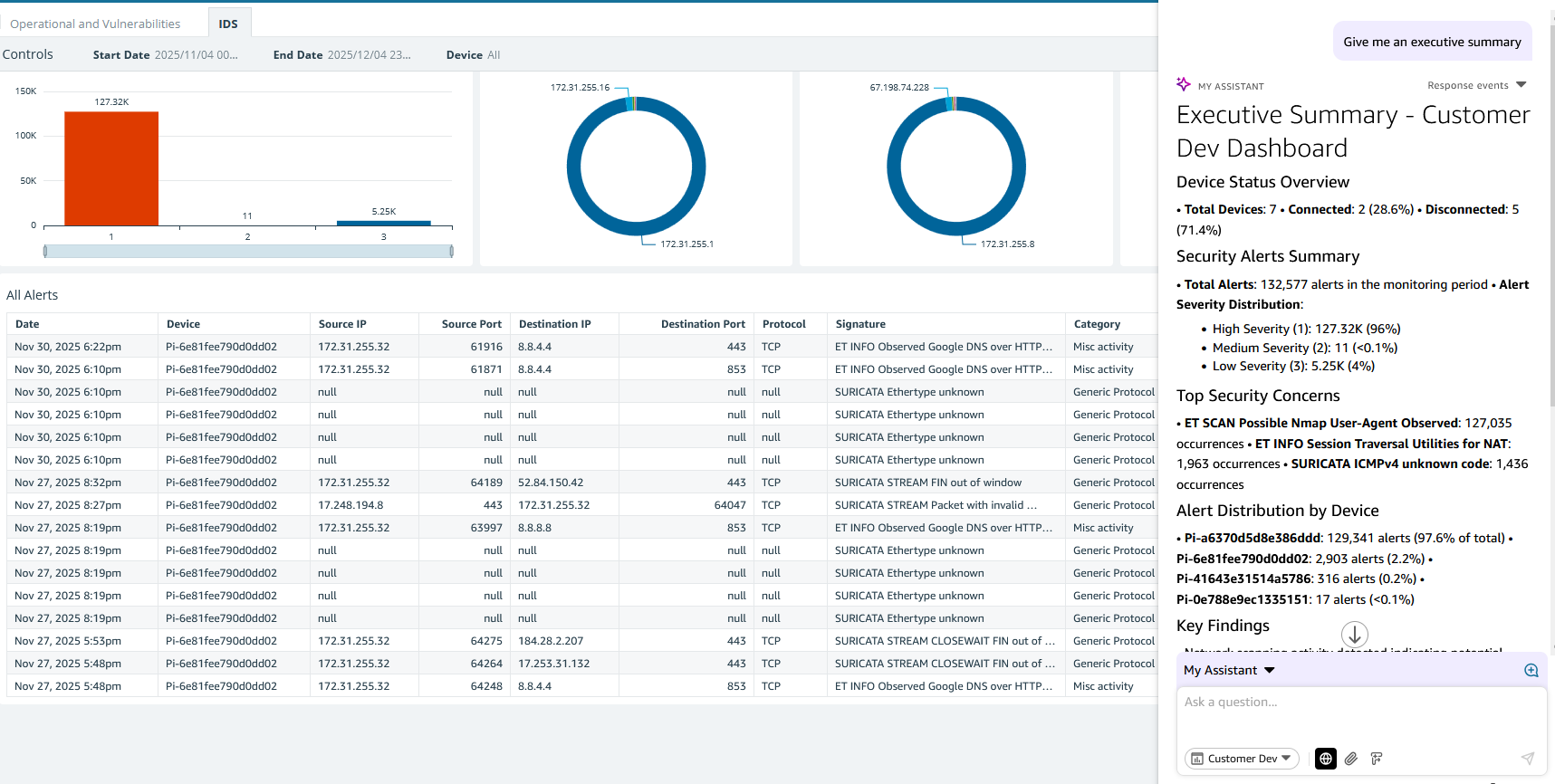
Intrusion Detection System
Monitor 132,000+ alerts across your entire network with real-time threat visualization.
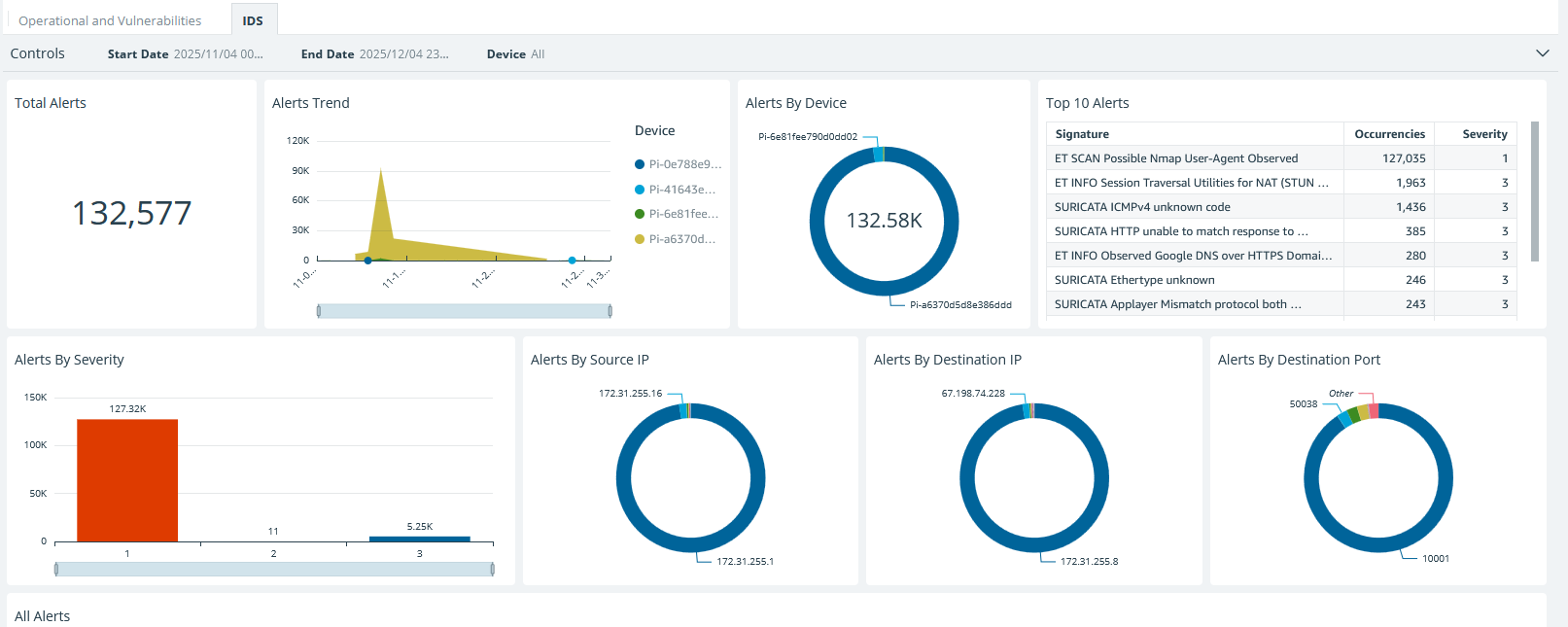
Complete Threat Visibility
Track alerts by device, severity, source IP, and destination port. Identify top security concerns instantly with SURICATA-powered detection.
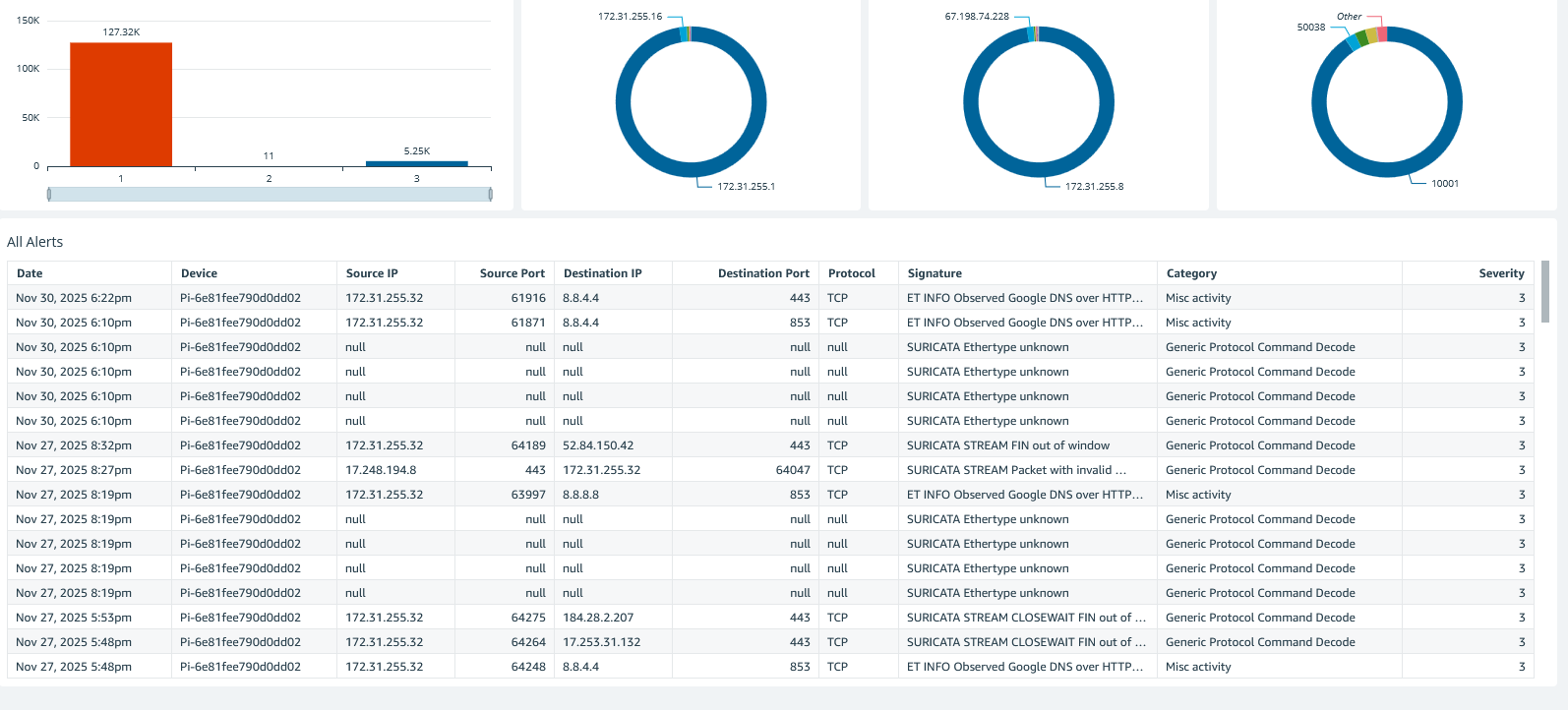
Detailed Alert Analysis
Drill down into individual alerts with full protocol details, signatures, and categorization.
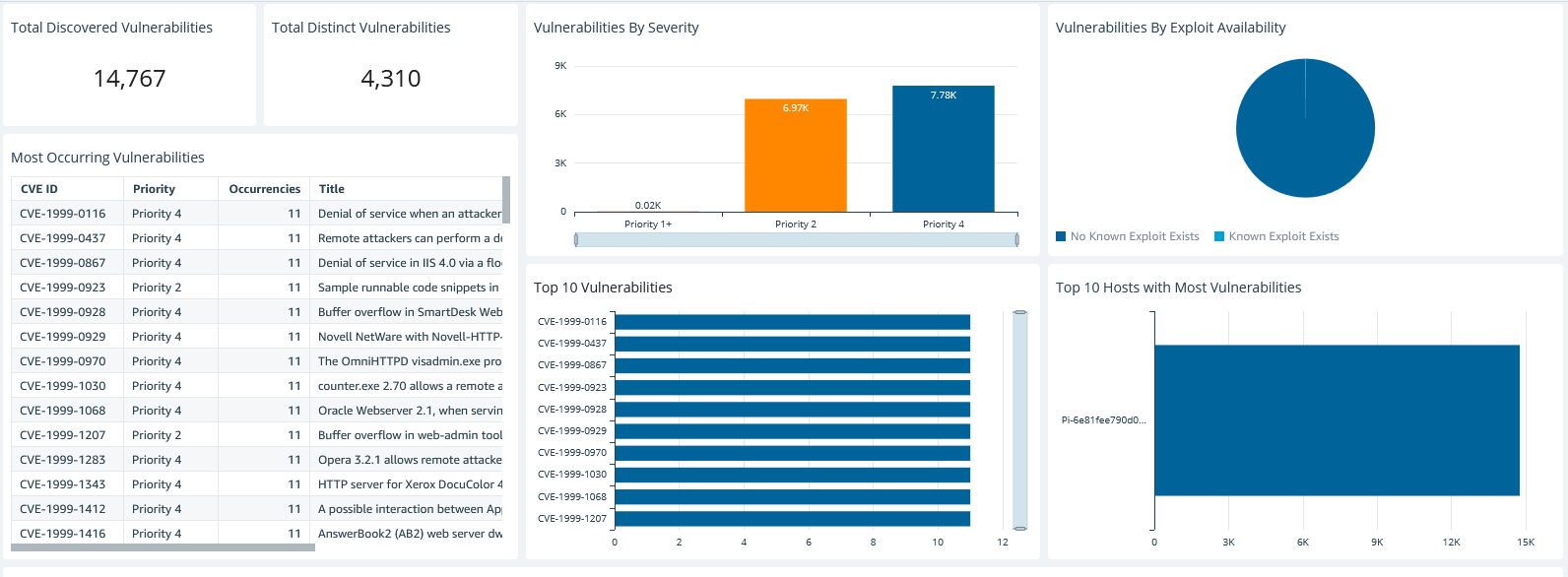
Vulnerability Assessment
14,767 discovered vulnerabilities across 4,310 distinct CVEs, prioritized by severity and exploit availability.
Operational Monitoring
Real-time visibility into device health, performance, and global distribution.

Global Device Mapping
Track connected and disconnected devices with geographic visualization. Know your asset status at a glance.

Resource Monitoring
Continuous CPU and RAM tracking ensures edge devices maintain optimal performance without impacting operations.
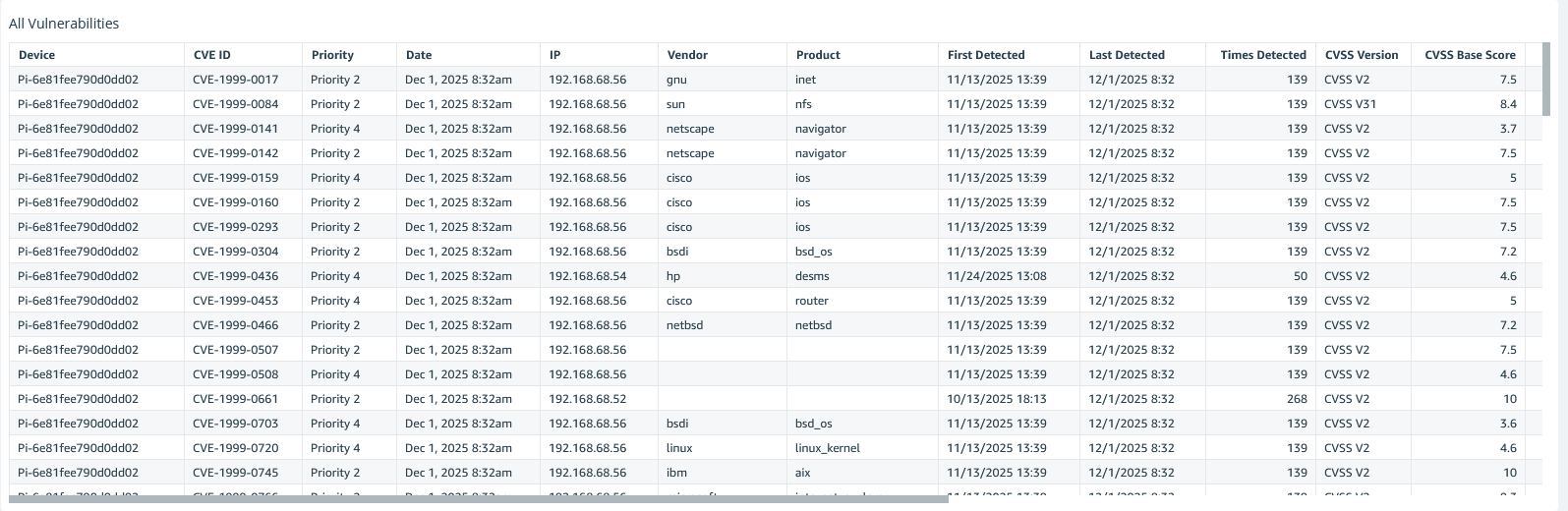
CVE Database Integration
Every vulnerability mapped to CVE IDs with vendor, product, CVSS scores, and detection timestamps for complete audit trails.
AI-Powered Security Assistant
Powered by Amazon Q — enterprise-grade AI that’s secured to your data alone.
🔒 Data Isolation
Your security data never leaves your environment. Amazon Q operates within your AWS boundary with zero external data sharing.
💬 Natural Language Queries
Ask questions like “Give me an executive summary” or “What are my top security concerns?” — get instant, contextual answers.
📊 Automated Summaries
Generate executive-ready reports on device status, alert distribution, and key findings with a single click.
🎯 Intelligent Prioritization
AI correlates alerts across devices and time to surface the threats that matter most — cutting through alert fatigue.
Edge Device Solutions
Purpose-built hardware for every environment — from small offices to enterprise data centers.
Edge S WiFi
1-20 devices- • WiFi monitoring
- • Small office deployment
- • Compact form factor
- • Plug-and-play setup
Edge S Dual-ETH
1-20 devices- • Dual Ethernet ports
- • Industrial environments
- • Wired network focus
- • OT/ICS compatible
Edge M
20-200 devices- • Mid-range capacity
- • Branch office ready
- • Enhanced processing
- • Multi-VLAN support
Edge L
200-500 devices- • Enterprise-grade
- • High throughput
- • Data center ready
- • Redundancy options